HNCTF2024逆向部分题解
Baby_OBVBS:
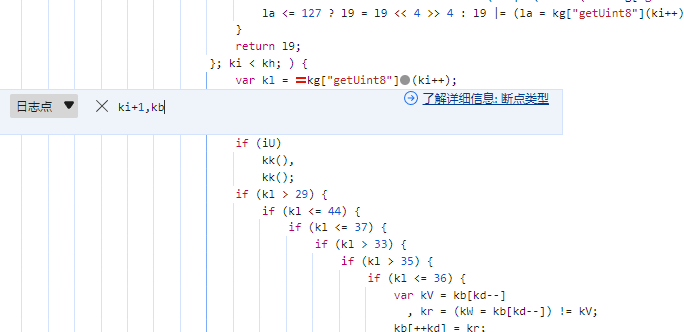
第一次做vbs的逆向题目,根本不知道怎么解决,看了看网上的教程,发现这个文件有很多Chr加密,所以我当时想要使用python将其提取出来,但是提取之后发现数据不全,所以只能放弃,看了大佬的WP之后,发现有更简单的方法,就是将前面的Execute改成 wscript.echo,然后就可以直接输出脚本内容了,真的厉害,tql了
修改前缀

[Visual Basic] 纯文本查看 复制代码
|
001
002
003
004
005
006
007
008
009
010
011
012
013
014
015
016
017
018
019
020
021
022
023
024
025
026
027
028
029
030
031
032
033
034
035
036
037
038
039
040
041
042
043
044
045
046
047
048
049
050
051
052
053
054
055
056
057
058
059
060
061
062
063
064
065
066
067
068
069
070
071
072
073
074
075
076
077
078
079
080
081
082
083
084
085
086
087
088
089
090
091
092
093
094
095
096
097
098
099
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
|
eAqi = "59fc6b263c3d0fcbc331ade699e62d3473bbf85522d588e3423e6c751ca091528a3c0186e460483917192c14"ANtg = "baacc7ffa8232d28f814bb14c428798b"Function Base64Decode(base64EncodedString) Dim xml, elem Set xml = CreateObject("MSXML2.DOMDocument") Set elem = xml.createElement("tmp") elem.dataType = "bin.base64" elem.text = base64EncodedString Dim stream Set stream = CreateObject("ADODB.Stream") stream.Type = 1 'Binary stream.Open stream.Write elem.nodeTypedValue stream.Position = 0 stream.Type = 2 'Text stream.Charset = "utf-8" Base64Decode = stream.ReadText stream.CloseEnd FunctionFunction Initialize(strPwd) Dim box(256) Dim tempSwap Dim a Dim b For i = 0 To 255 box(i) = i Next a = 0 b = 0 For i = 0 To 255 a = (a + box(i) + Asc(Mid(strPwd, (i Mod Len(strPwd)) + 1, 1))) Mod 256 tempSwap = box(i) box(i) = box(a) box(a) = tempSwap Next Initialize = boxEnd FunctionFunction Myfunc(strToHash) Dim tmpFile, strCommand, objFSO, objWshShell, out Set objFSO = CreateObject("Scripting.FileSystemObject") Set objWshShell = CreateObject("WScript.Shell") tmpFile = objFSO.GetSpecialFolder(2).Path & "\" & objFSO.GetTempName objFSO.CreateTextFile(tmpFile).Write(strToHash) strCommand = "certutil -hashfile " & tmpFile & " MD5" out = objWshShell.Exec(strCommand).StdOut.ReadAll objFSO.DeleteFile tmpFile Myfunc = Replace(Split(Trim(out), vbCrLf)(1), " ", "")End FunctionFunction EnCrypt(box, strData) Dim tempSwap Dim a Dim b Dim x Dim y Dim encryptedData encryptedData = "" For x = 1 To Len(strData) a = (a + 1) Mod 256 b = (b + box(a)) Mod 256 tempSwap = box(a) box(a) = box(b) box(b) = tempSwap y = Asc(Mid(strData, x, 1)) Xor box((box(a) + box(b)) Mod 256) encryptedData = encryptedData & LCase(Right("0" & Hex(y), 2)) Next EnCrypt = encryptedDataEnd Functionmsgbox "Do you know VBScript?"msgbox "VBScript (""Microsoft Visual Basic Scripting Edition"") is a deprecated Active Scripting language developed by Microsoft that is modeled on Visual Basic."msgbox "It allows Microsoft Windows system administrators to generate powerful tools for managing computers without error handling and with subroutines and other advanced programming constructs. It can give the user complete control over many aspects of their computing environment."msgbox "Interestingly, although VBScript has long since been deprecated, you can still run VBScript scripts on the latest versions of Windows 11 systems."msgbox "A VBScript script must be executed within a host environment, of which there are several provided with Microsoft Windows, including: Windows Script Host (WSH), Internet Explorer (IE), and Internet Information Services (IIS)."msgbox "For .vbs files, the host is Windows Script Host (WSH), aka wscript.exe/cscript.exe program in your system."msgbox "If you can not stop a VBScript from running (e.g. a dead loop), go to the task manager and kill wscript.exe/cscript.exe."msgbox "cscript and wscript are executables for the scripting host that are used to run the scripts. cscript and wscript are both interpreters to run VBScript (and other scripting languages like JScript) on the Windows platform."msgbox "cscript is for console applications and wscript is for Windows applications. It has something to do with STDIN, STDOUT and STDERR."msgbox "OK! Now, let us begin our journey."key = InputBox("Enter the key:", "CTF Challenge")if (key = False) then wscript.quitif (len(key)<>6) then wscript.echo "wrong key length!" wscript.quitend ifIf (Myfunc(key) = ANtg) Then wscript.echo "You get the key!Move to next challenge."Else wscript.echo "Wrong key!Try again!" wscript.quitEnd IfuserInput = InputBox("Enter the flag:", "CTF Challenge")if (userInput = False) then wscript.quitif (len(userInput)<>44) then wscript.echo "wrong!" wscript.quitend ifbox = Initialize(key)encryptedInput = EnCrypt(box, userInput)If (encryptedInput = eAqi) Then MsgBox "Congratulations! You have learned VBS!"Else MsgBox "Wrong flag. Try again."End Ifwscript.echo "bye!" |
根据代码尝试解密一下:
RC4解密:
根据初始化代码,我们可以发现这是一个RC4加密,前面已经给出了密文和key,其中key是MD5值,使用CMD5解密一下,得到key,H&NKEY,然后进行RC4解密
得到flag是H&NCTF{VBS_1s@s0_7unny_an4_pow3rfu1_t00l!}
本站资源来自互联网收集,仅提供信息发布
一旦您浏览本站,即表示您已接受以下条约:
1.使用辅助可能会违反游戏协议,甚至违法,用户有权决定使用,并自行承担风险;
2.本站辅助严禁用于任何形式的商业用途,若被恶意贩卖,利益与本站无关;
3.本站为非营利性网站,但为了分担服务器等运营费用,收费均为赞助,没有任何利益收益。
死神科技 » HNCTF2024逆向部分题解
一旦您浏览本站,即表示您已接受以下条约:
1.使用辅助可能会违反游戏协议,甚至违法,用户有权决定使用,并自行承担风险;
2.本站辅助严禁用于任何形式的商业用途,若被恶意贩卖,利益与本站无关;
3.本站为非营利性网站,但为了分担服务器等运营费用,收费均为赞助,没有任何利益收益。
死神科技 » HNCTF2024逆向部分题解